Security experts have identified three Android malware families that have infiltrated the Google Play Store and are concealing their harmful payloads inside several ostensibly innocent applications.
Users who downloaded the malicious apps experienced data theft, social media account hijacking, SMS interception, and unauthorized payments to their cell accounts.
The “Joker,” “Facestealer,” and “Coper” malware families were found in the Google Play Store by Zscaler’s ThreatLabz.
All applications were later taken off the Play Store when the analysts alerted Google of their findings. However, those who continue to use these malicious apps must uninstall them and carry out a device lean-up to uproot any leftovers.
Contents
The Joker
A member of the Joker virus family will subscribe mobile numbers to expensive wireless application protocol (WAP) services while also stealing data from infected devices, such as SMS messages and the victim’s contact list.
According to Zscaler’s analysis, there are 50 applications trojanized with Joker that together have received over 300,000 Play Store downloads.
It is simpler for malware to obtain the high-level capabilities required for its destructive operation since almost half of them are communication applications, which naturally need users to allow access to dangerous permissions.
The payload is currently concealed by the Joker developers as a shared asset file in base64-obfuscated form, occasionally with a JSON, TTF, PNG, or database file extension.
According to Zscaler in the research, “Many Joker applications conceal the payload in the assets folder of the Android Package Kit (APK) and construct an ARM ABI executable to escape detection by most sandboxes which are built on x86 architecture.”
The Facestealer
Facestealer, as implied by the name of the virus, uses false login forms overlayed on top of authentic app login forms to steal victims’ Facebook accounts.
The researchers discovered one software, a seemingly trustworthy program called “Vanilla Snap Camera,” that included the specific virus family hidden in its code.
The Coper
Coper is an information-stealing virus that can send malicious SMS texts, execute overlay assaults, log text written on the devices, intercept SMS messages, and transfer data back to the attacker’s servers.
Analysts at Zscaler discovered at least one app with the name “Unicc QR Scanner” that had 1,000 infected devices due to Coper being hidden in its code.
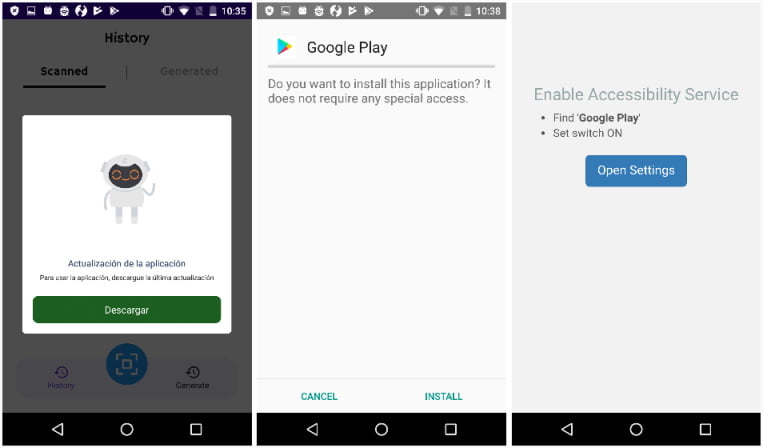
The app does not include any harmful code when it is first downloaded, but after it has been activated and installed, it will download the malware through a phony software update.
Guidelines for safety from Malicious Apps
Install only absolutely necessary apps from the Google Play Store, check reviews before installing an app to see whether anybody has reported harmful behavior, and only trust big, well-known publishers to reduce the likelihood of getting a malicious app.
When installing an app, pay close attention to the permissions that are asked and avoid allowing access to hazardous ones, especially if they don’t appear to be related to the program’s primary features.
Last but not least, make sure Play Protect is turned on for your device and routinely check your network data and battery use to find any possibly suspicious applications that could be running.