Are you tired of online impersonation and phishing scams? iOS 17.2 delivers a powerful shield in the form of Contact Key Verification; a cutting-edge security feature that lets you double-check the identity of the person you’re texting. This guide allows you to take charge of your communication security, whether you’re facing targeted attacks, an activist advocating sensitive material, or just someone who values digital privacy.
Contents
Why It’s Important:
Impersonation and disinformation may thrive in the internet world. Imagine receiving urgent messages from someone who looks to be a close friend, only to find out it’s a clever fraudster.
Contact Key Verification combats this, offering an extra layer of trust and assurance, especially for those at heightened risk in their digital interactions.
How It Works:
This revolutionary feature leverages cryptographic technology to generate unique “keys” for your device and those of your contacts. When enabled, both parties can compare these keys through various methods, ensuring you’re truly communicating with the intended person.
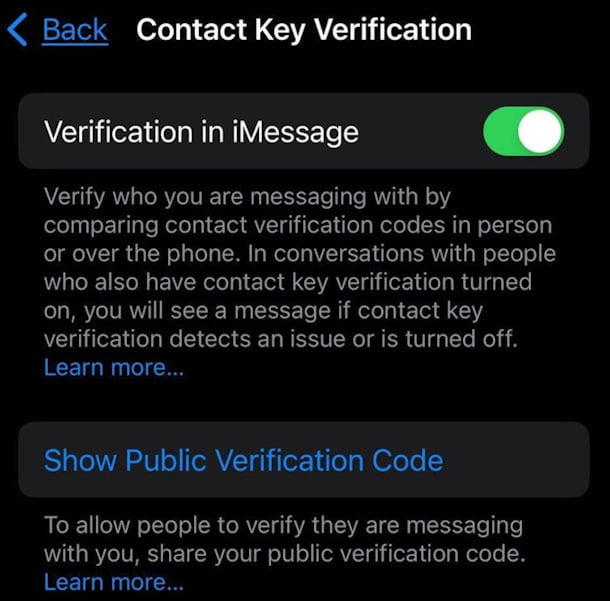
Enabling Contact Key Verification:
- Open Settings and tap your Apple ID.
- Scroll down and select Contact Key Verification.
- Toggle on Verification in iMessage.
- Follow the prompts to update any incompatible devices (recommended for optimal security).
Verifying Contacts:
Once enabled, you have two options:
1. Sharing your Public Verification Code:
- Tap Show Public Verification Code.
- Copy and share this unique string with your contact through a secure channel.
- Your contact can compare this code with the one displayed on your online profile (e.g., social media bio) to verify your identity.
2. Generating Verification Codes in Messages:
- Open a conversation with your contact.
- Tap their name and select Verify Contact.
- Both devices will display six-digit codes.
- If the codes match, tap Mark as Verified to establish trust.
- If they don’t match, proceed with caution and consider alternative communication methods to confirm their identity.
Benefits of Contact Key Verification:
- Enhanced Protection: Provides an extra layer of security against impersonation and phishing scams.
- Peace of Mind: Verifies the authenticity of your contacts, especially for high-risk individuals.
- Granular Control: Choose the verification method best suits your needs and communication style.
- Future-Proof Security: Paves the way for more secure communication protocols in the digital landscape.
Beyond the Basics:
- This feature is still evolving, with future updates expected to expand its capabilities and integration with other communication platforms.
- Remember, both parties need Contact Key Verification enabled for it to function effectively.
- While not foolproof, this tool significantly reduces the risk of online deception and empowers you to take charge of your digital security.
Embrace the Future of Secure Communication:
iOS 17.2’s Contact Key Verification marks a significant leap forward in online security. By understanding and implementing its power effectively, you can navigate the digital world with greater confidence and trust. This advanced tool is not just for high-profile individuals; it empowers everyone to take control of their online interactions and build safer, more secure communication channels.
Bonus Tip: Stay informed! Keep your iOS version updated to benefit from the latest security features and bug fixes.
By harnessing the power of Contact Key Verification, you can unlock a future of secure and trusted communication, where online connections are truly built on authenticity and trust.